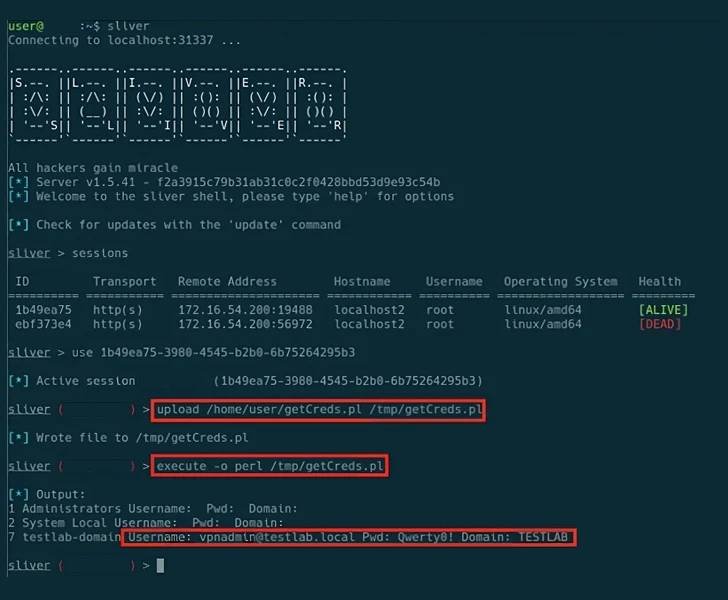
“The Five Eyes Intelligence Alliance Issues Cybersecurity Warning on Active Exploitation of Ivanti Gateway Vulnerabilities
The Five Eyes (FVEY) intelligence alliance has issued a cybersecurity advisory cautioning about cyber threat actors taking advantage of known security vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure gateways. The advisory emphasizes that the Integrity Checker Tool (ICT) employed by Ivanti can be deceived, providing a false sense of security and allowing cyber threat actors to achieve root-level persistence even after factory resets.
Ivanti has disclosed five security vulnerabilities in its products since January 10, 2024, with four actively exploited by multiple threat actors to deploy malware. The vulnerabilities include authentication bypass, command injection, privilege escalation, and server-side request forgery (SSRF) issues.
Mandiant’s analysis revealed the placement of an encrypted version of the BUSHWALK malware in a directory excluded by ICT, enabling threat actors to bypass integrity checks. Eclypsium had previously highlighted the tool’s directory exclusions, allowing attackers to leave behind backdoors undetected.
The advisory recommends network defenders to assume the possibility of sophisticated threat actors deploying rootkit-level persistence even on devices that have undergone resets. Organizations are urged to carefully evaluate the risk of adversary access and persistence on Ivanti Connect Secure and Ivanti Policy Secure gateways when deciding to continue using these devices in an enterprise environment.
In response to the advisory, Ivanti stated it is unaware of any instances of successful threat actor persistence following security updates and factory resets. The company is also releasing a new version of ICT to enhance visibility into a customer’s appliance and all files present on the system.”