Chinese internet users searching for legitimate software like Notepad++ and VNote on platforms such as Baidu are falling victim to malicious advertisements and fraudulent links that distribute trojanized versions of the software, ultimately deploying Geacon, a Golang-based implementation of Cobalt Strike.
According to Sergey Puzan, a researcher at Kaspersky, the malicious site discovered in the search results for Notepad++ is being spread through an advertisement block.
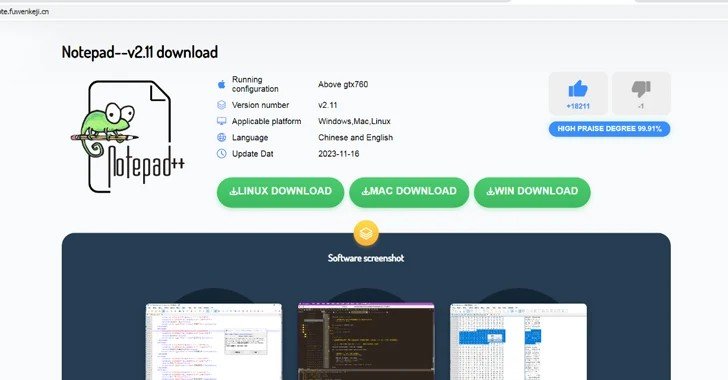
Upon accessing the site, observant users may notice a discrepancy: the website URL includes “vnote,” the title suggests a download for Notepad‐‐ (a counterpart of Notepad++), while the displayed image depicts Notepad++.
However, the packages downloaded from the site actually contain Notepad‐‐.
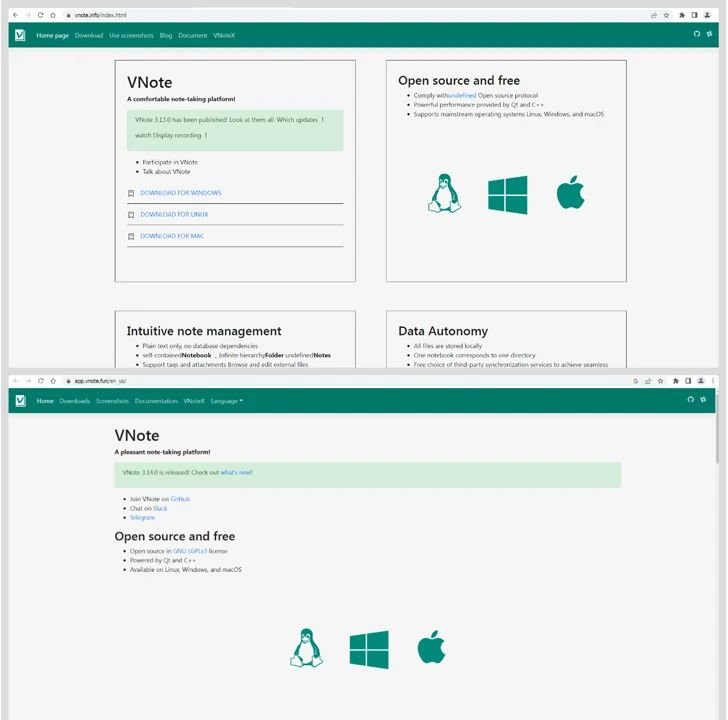
Similarly, fake websites impersonating VNote (“vnote[.]info” and “vnotepad[.]com”) redirect users to the same set of myqcloud[.]com links, which in this case also point to a Windows installer hosted on the domain. However, the links to potentially malicious versions of VNote are no longer active.
An examination of the altered Notepad– installers reveals their design to retrieve a next-stage payload from a remote server, functioning as a backdoor with traits resembling Geacon. T
his backdoor is capable of establishing SSH connections, performing file operations, enumerating processes, accessing clipboard content, executing files, uploading and downloading files, capturing screenshots, and entering sleep mode. Command-and-control (C2) is enabled via the HTTPS protocol.
These developments coincide with malvertising campaigns that have served as conduits for other malware, such as FakeBat (also known as EugenLoader) malware, using MSIX installer files disguised as Microsoft OneNote, Notion, and Trello.